Introduction
In today’s digital landscape, ensuring the security and privacy of DNS (Domain Name System) queries has become increasingly critical. Traditional DNS queries over the internet are transmitted in plaintext, making them vulnerable to various types of attacks, such as DNS spoofing, man-in-the-middle attacks, and DNS cache poisoning. These vulnerabilities can lead to data breaches, privacy violations, and system compromises. To mitigate these risks, implementing DNS over TLS (DoT) as a forwarder for DNS Server can provide a secure and encrypted channel for DNS queries, safeguarding them from prying eyes.


Use DNS over TLS Forwarders in Active Directory DNS Environment
In this blog post, I will outline a solution for using DNS over TLS in a Windows Active Directory (AD) environment. Since the AD DNS Server does not natively support DoH (DNS over HTTPS) or DoT, we will employ a workaround by setting up Stubby DNS on a standalone Linux machine. Stubby will act as an intermediary, forwarding DNS queries securely over TLS to trusted DNS providers such as DNS by Google and Cloudflare. Let’s dive into the setup process.
Redundancy: You may also use 2 VMs or Docker containers to get redundancy.
PS: Though Windows client machines like Windows 11 support DNS over HTTPS (DoH), we can use secure public DNS. However, in the Active Directory Environment, we must use the corporate LAN Network AD DNS server for domain-joined machines (which work in a private trusted office network). Then AD DNS servers have to forward the request to public DNS (here we need security).
Prerequisites
- A standalone Linux machine to install Stubby DNS
- Windows Server running Active Directory with DNS role installed
- Basic knowledge of DNS configuration in Active Directory
Step-by-Step Setup
Step 1: Installing Stubby DNS on Linux
First, we need to install Stubby DNS on our standalone Linux machine. Stubby is an open-source DNS Privacy Daemon that supports DNS over TLS.
- Install Dependencies:
sudo apt update
sudo apt install -y stubby2. Verify Installation:
stubby -hThis command should display the help message for Stubby, confirming that it is installed correctly.
Step 2: Configuring Stubby DNS
Next, we need to configure Stubby to use DNS over TLS with Google and Cloudflare as our DNS providers.
- Edit the Stubby Configuration File: Open the Stubby configuration file in your preferred text editor:
sudo nano /etc/stubby/stubby.yml2. Add DNS Providers Configuration: Add the following configuration to use Google and Cloudflare as DNS providers
upstream_recursive_servers:
- address_data: 8.8.8.8
tls_auth_name: "dns.google"
- address_data: 8.8.4.4
tls_auth_name: "dns.google"
- address_data: 1.1.1.1
tls_auth_name: "cloudflare-dns.com"
- address_data: 1.0.0.1
tls_auth_name: "cloudflare-dns.com"In the default stubby.yml file the above-mentioned DNS servers along with many others are already added, you just need to uncomment your desired providers

3. Change Stubby DNS Port to 53: By default, Stubby listens on port 8053. We need to change this to port 53 to ensure compatibility with the AD DNS server
listen_addresses:
- 127.0.0.1@534. Round Robin DNS setting: I have used 2 DNS providers so it has been set up in a round-robin scenario, if you need to disable it use it in an order list, please change it to 0.
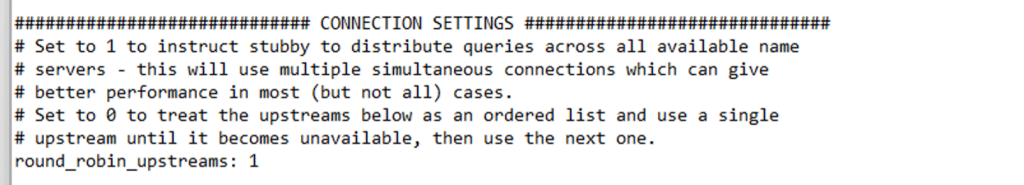
5. Save and Close the Configuration File: Save the changes and close the text editor.
6. Restart Stubby DNS Service
sudo systemctl restart stubby
sudo systemctl enable stubbyStep 3: Configuring Active Directory DNS Server
Now that Stubby is configured to use DNS over TLS, we need to set up the AD DNS server to forward DNS queries to Stubby.
- Open DNS Manager: On your Windows Server, open DNS Manager.
- Configure Forwarders:
- Right-click on the DNS server and select “Properties”.
- Go to the “Forwarders” tab.
- Click on “Edit” and add the IP address of your Stubby DNS server (e.g.,
172.16.1.10). - Click “OK” to save the changes.
- Uncheck the “use root hints if no forwarders are available”.
- Click “Apply” & “OK”.

Step 4: Verifying the Setup
To ensure that the setup is working correctly, you can perform the following tests:
- Check DNS Query Resolution: On a client machine joined to the AD domain, perform a DNS query using
nslookup:
nslookup example.comVerify that the query is resolved correctly.
2. Verify Secure DNS Resolution: On the Linux machine running Stubby, you can use tools like tcpdump to capture and inspect DNS traffic, ensuring that it is being transmitted securely over TLS.
Complete Flow of DNS Queries
The complete flow of DNS queries in this setup is as follows:
- Client Machine: A domain-joined client machine makes a DNS query.
- AD DNS Server: The query is sent to the AD DNS Server.
- Stubby DNS: The AD DNS Server forwards the query to the Stubby DNS server on port 53.
- DNS Providers: Stubby DNS forwards the query over a secure TLS connection (port 853) to the configured DNS providers (Google and Cloudflare).
- Response: The DNS response is received by Stubby over TLS, which then sends it back to the AD DNS Server.
- Client Machine: The AD DNS Server forwards the response back to the client machine.
DNS Security Threats and Vulnerabilities
By implementing DNS over TLS, we mitigate various DNS-related threats and vulnerabilities, including:
- DNS Spoofing: Attackers can forge DNS responses to redirect users to malicious websites.
- Man-in-the-Middle Attacks: Interceptors can alter DNS queries and responses during transmission.
- DNS Poisoning: Malicious data can be injected into the DNS cache, causing users to be directed to incorrect sites.
- Data Privacy Violations: Unencrypted DNS queries can be monitored, revealing user activity and patterns.
Conclusion
Securing DNS queries in a Windows Active Directory environment is crucial for protecting against various DNS vulnerabilities. By setting up Stubby DNS on a standalone Linux machine and configuring it to use DNS over TLS with trusted providers like Google and Cloudflare, we can ensure that our DNS queries are encrypted and secure. This solution provides an effective workaround for environments where the AD DNS server does not natively support DoH or DoT, enhancing the overall security posture of your network.
For more information on Stubby DNS and DNS privacy, refer to the Stubby DNS Documentation, Google Public DNS, Cloudflare DNS
Further Reads:
20 Essential PowerShell Commands for Active Directory Management
How to Secure Active Directory: Best Practices and Pro Tips
Essential Network Ports for Active Directory, DNS, DHCP, and ADFS
DNS Error | A new record cannot be created
- Why should you automate Active Directory cleanup? - 17 June 2025
- Troubleshooting: Unable to Add Instance Failover Group to Azure SQL Managed Instance - 4 March 2025
- 10 Azure Virtual Desktop (AVD) Cost-Optimization Strategies for 2025 💡💰 - 22 February 2025